Exterro’s FTK is a court-accepted digital investigations platform that is built for speed, analytics and enterprise-class scalability. Known for its intuitive interface, email analysis, customizable data views and stability, FTK lays the framework for seamless expansion, so your computer forensics solution can grow with your organization’s needs.
Exterro’s FTK is a court-accepted digital investigations platform that is built for speed, analytics and enterprise-class scalability. Known for its intuitive interface, email analysis, customizable data views and stability, FTK lays the framework for seamless expansion, so your computer forensics solution can grow with your organization’s needs.
In addition, Exterro offers new expansion modules delivering an industry-first malware analysis capability and state-of-the-art visualization. These modules integrate with FTK to create the most comprehensive computer forensics platform on the market.
Cerberus
Cerberus is a malware triage technology that is available as an add-on for FTK. The first step towards automated reverse engineering, Cerberus provides threat scores and disassembly analysis to determine both the behavior and intent of suspect binaries.
Features:
INTEGRATED COMPUTER FORENSICS SOLUTION
Create images, process a wide range of data types from forensic images to email archives, analyze the registry, conduct an investigation, decrypt files, crack passwords, and build a report all with a single solution. Recover passwords from 100+ applications. KFF hash library with 45 million hashes. Advanced, automated analysis without scripting.
SINCE FTK IS DATABASE DRIVEN, IT MEANS YOU DON’T LOSE WORK DUE TO CRASHING
Unlike other products on the market, FTK is database driven so you won’t experience the crashing associated with memory-based tools. In addition, FTK components are compartmentalized, so for example, if the GUI crashes, the processing workers continue to process data.
UNMATCHED PROCESSING
FTK is different from other computer forensics solutions in that it processes data up front, so you’re not wasting time waiting for searches to execute during the analysis phase. However, the product is designed to provide the fastest, most accurate and consistent forensic processing possible with distributed processing and true multi-threaded / multi-core support. Every copy of FTK includes a total of 4 processing workers – 1 on the examiner machine and 3 distributed. If you are interested in having multiple examiners share a common processing farm and centralized database for collaborative analysis, please contact your sales representative to inquire about Access Data Lab. Wizard-driven processing ensures no data is missed. Cancel/Pause/Resume functionality Real-time processing status CPU resource throttling
Email notification upon processing completion Pre- and post-processing refinement Advanced data carving engine allows you to specify criteria, such as file size, data type and pixel size to reduce the amount of irrelevant data carved while increasing overall thoroughness.
SINGLE-NODE ENTERPRISE
Install a persistent or “dissolving” agent on a single computer to enable the remote analysis and incident response capabilities of AD Enterprise. Preview, acquire and analyze hard drive data, peripheral device data, and volatile/memory data on Apple®, UNIX® and Linux® operating systems. Uninstall the agent at any time and push it out to a different computer for multi-machine analysis. Easy, wizard-driven agent deployment. Secure remote device mounting using the Pico agent.
ADVANCED VOLATILE / MEMORY ANALYSIS
Supports Windows® (32- and 64-bit), Apple®, UNIX® and Linux® operating systems Comprehensive analysis of volatile data Static RAM analysis from an image or against a live system Enumerate all running processes, including those hidden by rootkits, and display associated DLLs, network sockets and handles in context. Dump a process and associated DLLs for further analysis in third-party tools. Memory string search allows you to identify hits in memory and automatically map them back to a given process, DLL or piece of unallocated space and dump the corresponding item. FTK now provides VAD tree analysis and exposes registry artifacts in memory and will parse and display handle information from memory.
FASTER, MORE COMPREHENSIVE INDEX AND BINARY SEARCHING
FTK processes and indexes your data up front, so search and analysis is faster than other products. Leveraging the powerful dtSearch engine, as well as a full-featured regular expression engine, FTK produces fast and accurate results. New in FTK: Regular expression support in index searching allows you to search for advanced combinations of characters within indexed data.
BROAD FILE SYSTEM. FILE TYPE AND EMAIL SUPPORT
Support for 700+ image, archive and file types Notes NSF, Outlook PST/OST, Exchange EDB, Outlook Express DBX, Eudora, EML (Microsoft Internet Mail, Earthlink, Thunderbird, Quickmail, etc.), Netscape, AOL and RFC 833Process and analyze DMG (compressed and uncompressed), Ext4, exFAT, VxFS (Veritas File System), Microsoft VHD (Microsoft Virtual Hard Disk), Blackberry IPD backup files, Android YAFFS / YAFFS 2 and many more. Create and process Advanced Forensic Format (AFF) images.
EXPLICIT IMAGE DETECTION (EID) ADD-ON
This image detection technology not only recognizes flesh tones but has been trained on a library of more than 30,000 images to enable auto-identification of potentially pornographic images.
RICH REPORTING
Generate detailed reports in native format, HTML, PDF, XML, RTF, and more – with links back to the original evidence. Define Registry Supplemental Reports (RSR) during pre-processing or additional analysis. See which files could not be processed or indexed with the Processing Exception/Case Info report. Create a CSV of processed files that can be imported into Excel or a database application. Export MSGs for all supported email types.
Full-Disk Forensic Images
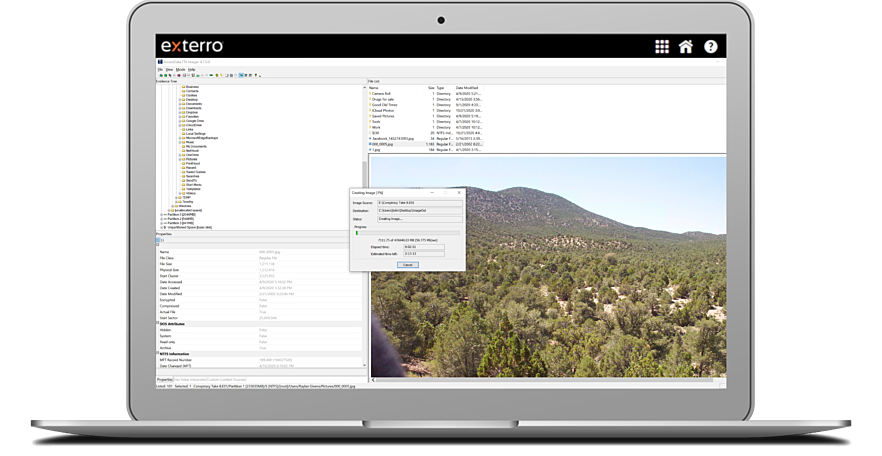
Create full-disk forensic images and process a wide range of data types from many sources, from hard drive data to mobile devices, network data and Internet storage, all in a centralized, secure database. FTK® processes and indexes data upfront, eliminating wasted time waiting for searches to execute. Cut down on OCR time by up to 30% with our efficient OCR engine.
Decrypt Files & Crack Passwords
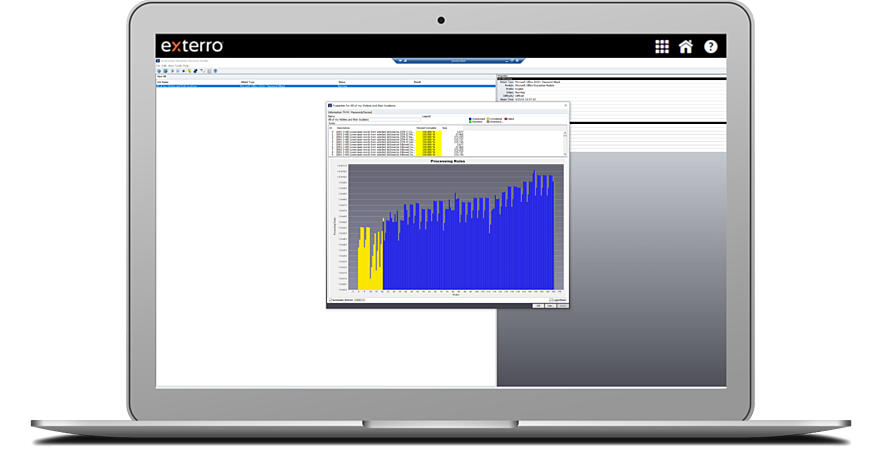
Decrypt files, crack passwords, and build reports with a single solution. Recover passwords from over 100+ applications. Decrypt a computer drive encrypted by the latest version of McAfee Drive Encryption and features L01 export support, which eases the workflow of users when data must be used within multiple tools.
Automatically decrypt (with proper credentials) Credant, SafeBoot, Utimaco, SafeGuard Enterprise and Easy, EFS, PGP, GuardianEdge, Pointsec and S/MIME.FTK is the only computer forensics solution that can identify encrypted PDFs.
Parse Registry Files
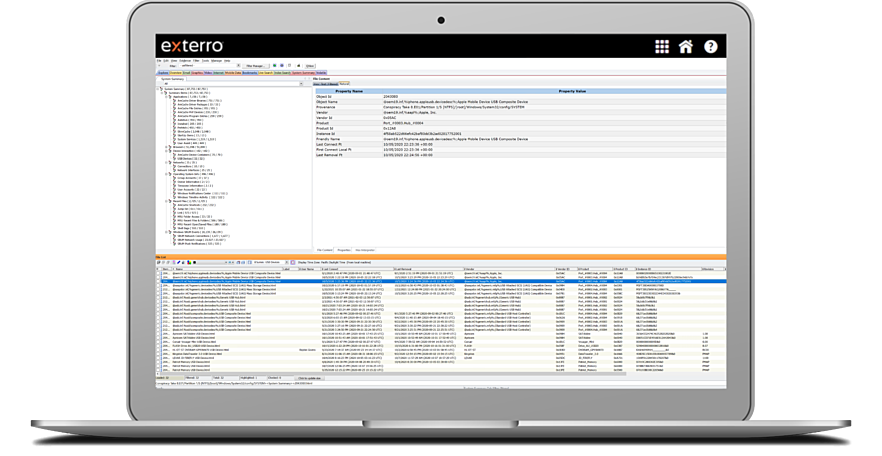
Parse registry files and Windows system information files in an easy to read, interactive and reportable tab. Label, bookmark and export individual objects per category, allowing for easy searching, filtering and reporting.
Locate, Manage and Filter Mobile Data
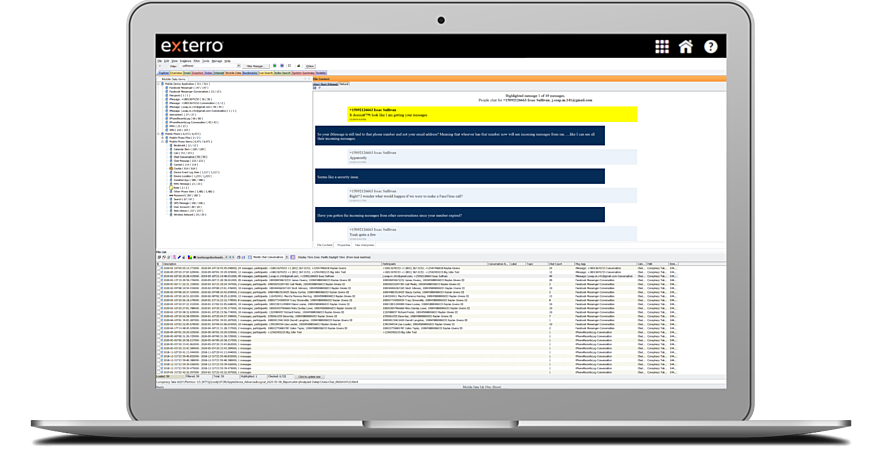
Locate, manage and filter mobile data more easily with a dedicated mobile tab. Use the message application filter to quickly isolate data from message applications like WhatsApp or Facebook.
Collect, Process and Analyze Datasets Containing Apple File Systems
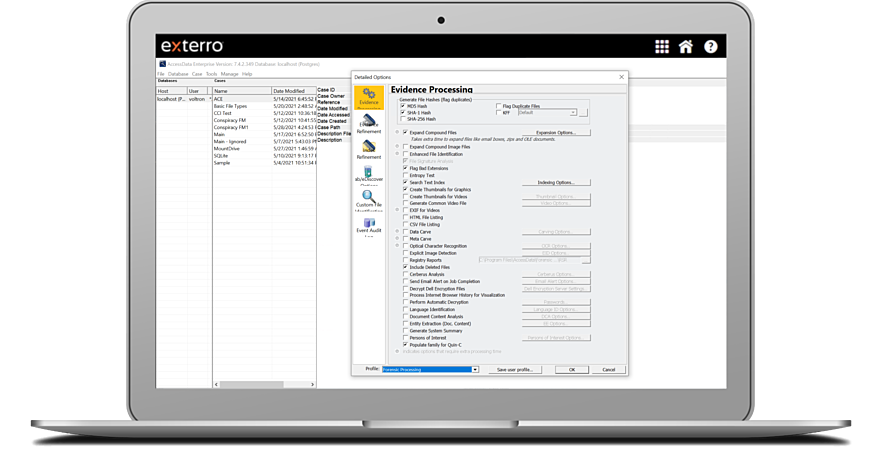
Collect, process and analyze datasets containing Apple file systems that are encrypted, compressed or deleted. FTK® Supports decryption of File Vault 2 from the APFS file system, as well as importing and parsing of AFF4 images created from Mac® computers (generated by third-party solutions like Cellebrite Digital Collector).
Process B-Trees attributes for metadata PLIST support SQLite database support Apple DMG and DD_DMG disk image support JSON file support
Visualization Technology
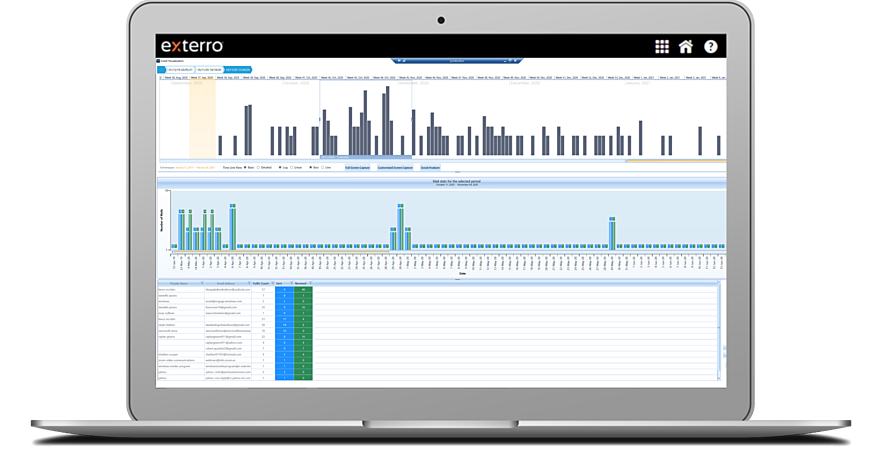
Visualization technology helps you get a clearer picture of events by displaying your data in timelines, cluster graphs, pie charts, geolocations, and more. Dig deeper and view all EXIF data, including location, make and model of the device used to capture images or video